Maintain network security and troubleshoot network problems
Network packet analyzer is a computer program that intercepts and analyzes the
network traffic.
Information flows in the network in binary data format and packet analyzers convert captured
data into a human-readable format and present this data in GUI.
The most common use of the network packet analyzers is to control, troubleshoot and maintain the network security by network administrators and to debug applications traffic by developers.
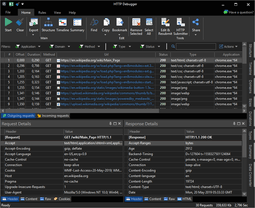
HTTP Debugger is an example of a network packet analyzer for Windows that intercepts network traffic by using the Man-in-the-Middle technique and can decode the SSL traffic.
Administrators can use a packet analyzer to perform a number of tests for a network. For example, they can simulate the injection attacks, identify the weakness of the network and solve the found vulnerabilities.
Developers use packet analyzers to debug the network traffic from their applications, identify and eliminate integration issues with third-party systems and troubleshoot weird situations, such as undocumented features and bugs while accessing these services.
The most common use of the network packet analyzers is to control, troubleshoot and maintain the network security by network administrators and to debug applications traffic by developers.
Logging Network Traffic
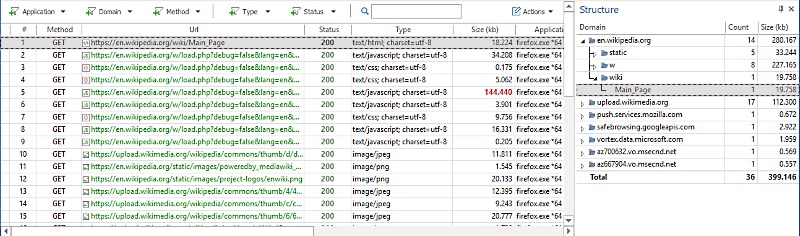
Logging network traffic is the primary task of network packet analyzers. Most packet analyzers sniff network traffic by putting the network interface card into a so-called promiscuous mode. This allows the network sniffer to see all packets its network segment and capture all data without processing. Another method for capturing network traffic is called Man-in-the-Middle (MITM). Packet sniffers using the MITM technique can only capture traffic for the host computer, but unlike analyzers using the NIC promiscuous mode, they can also decode SSL traffic.HTTP Debugger is an example of a network packet analyzer for Windows that intercepts network traffic by using the Man-in-the-Middle technique and can decode the SSL traffic.

Analyzing Network Packets
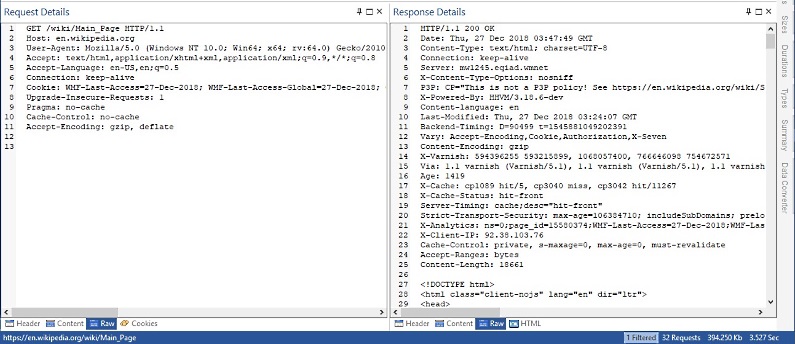
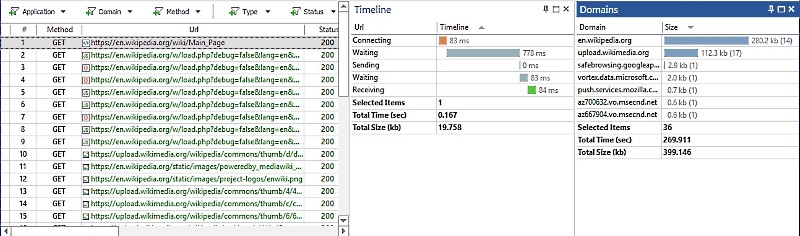
Network packet analyzers have built-in decoders for common protocols such as HTTP or FTP, and can reassemble transmitted files and HTTP streams into their original form and display in GUI or save to the local hard drive. For application-layer protocols such as HTTP, network protocol analyzer can display vital information about time spent to establish the network connection, time spent to send data and time spent to receive data.
Common Uses of Network Packet Analyzers
Network administrators use packet analyzers to collect network statistics, discover the network latency, troubleshoot the network problems, test the efficiency of firewalls and access control lists and to protect the local network from injection attacks.Administrators can use a packet analyzer to perform a number of tests for a network. For example, they can simulate the injection attacks, identify the weakness of the network and solve the found vulnerabilities.
Developers use packet analyzers to debug the network traffic from their applications, identify and eliminate integration issues with third-party systems and troubleshoot weird situations, such as undocumented features and bugs while accessing these services.
Three Principles of Networking Security
The concept of a secure system is based on three principles of the security model. If these three principles are met, the system is considered safe. These three important parts of security are: availability, integrity, and confidentiality and are known as the CIA triangle or the AIC triad.
1. Availability
The concept of availability can be explained as a guarantee of easy access to information by authorized users whenever they wish. Generally, authorized users should be able to access the data without any disturbance, every time and in the desired format. For this to happen, the system, the access channels, and the authentication mechanisms must always be working. It is essential to update and update the method, keep backup copies to protect data loss, the use of firewalls and proxy servers must be considered in a system to keep the data available.2. Integrity
Integrity is another vital principle to maintain a secure system and it is defined as the way to protect the stored data and avoid its destruction or modification by unauthorized users. To maintain integrity, the data should not be easily accessible to anybody and just authorized network administrators or people should be able to modify and monitor the stored data. As a result, integrity plays an important role in providing precise data with consistency and maintaining its reliability.3. Confidentiality
The concept of confidentiality in the AIC triad refers to privacy. In other words, the personal information of an individual should not get to the wrong hands. For example, the numbers of credit cards and personal information should just be in the hands of the intended user. This type of personal information is very much sensitive and information in the wrong hands can result in identity theft at great losses.
Copyright Notice: Please don't copy or translate this article without prior written permission
from the HTTPDebugger.com
HTTP Debugger is a proxy-less HTTP analyzer for developers that provides the ability to capture and analyze HTTP headers,
cookies, POST params, HTTP content and CORS headers from any browser or desktop application.
Awesome UI and very easy to use. Not a proxy, no network issues!
Download FREE 7-Day Trial
HTTP Debugger
 Debug HTTP API calls to a back-end and between back-ends.
Very easy to use.
Not a proxy, no network issues!
Download Free Trial
Debug HTTP API calls to a back-end and between back-ends.
Very easy to use.
Not a proxy, no network issues!
Download Free Trial



